Overview
Hello and Welcome Hacknet Apprentice! In this guide, I will go over Hacknet itself, How the commands are used, Diffrent Factions or Groups in Hacknet, what to do when stuck, how Hacknet is more realistic than other Hacking Simulator Games, and more! This Guide is recommended for Players who are new to this Genre, type of game and a bit of UNIX (Which is what the game uses, especially for it’s commands.)
~/Introduction/
#Hello and Welcome Hacknet Apprentice! In this guide, I will go over Hacknet itself, How the commands are used, Diffrent Factions or Groups in Hacknet, what to do when stuck, how Hacknet is more realistic than other Hacking Simulator Games, and more! This Guide is recommended for Players who are new to this Genre, type of game and a bit of UNIX (Which is what the game uses, especially for it’s commands.)
#
#
#What is Hacknet or HacknetOS & What it has (~/home/Hacknet.txt)
#The Main Features Explained (~/home/Features.txt)
#[NEW] Trace(d) Explained (~/bin/Trace.docx)
#[NEW] SSHCrack.exe (~/bin/SSHCrack.exe)
//More will be included in the Future!
—————————————————————–
-END OF INTRODUCTION-
~/log
—————————————————————————————————————————–
—————————————————————————————————————————–
@1_LOCAL_ADMIN_GuideCreated-9/10/2015
@2_LOCAL_ADMIN_DirectoryCreated_~/Introduction/
@3_LOCAL_ADMIN_DirectoryCreated_~/home/
@4_LOCAL_ADMIN_FileUploaded_”Hacknet.txt”_~/home/-9/10/2015
@5_LOCAL_ADMIN_FileUploaded_”Features.txt”_~/home/-9/10/2015
@6_LOCAL_ADMIN_DirectoryCreated_~/bin/_-9/20/2015
@7_LOCAL_ADMIN_FileUploaded_”Trace.docx”_~/bin/-9/20/2015
@8_LOCAL_ADMIN_FileUploaded_”SSHCrack.exe”_~/bin/-9/20/2015
~/home/Hacknet.txt
#As described by the Team who developed Hacknet(OS),
#
“Hacknet is a modern, super immersive terminal-driven hacking game with a fully internally-consistent network simulation and an interface so real you shouldn’t play it in an airport.
It follows the story of recently deceased hacker “Bit”, whose death may not be the ‘accident’ the media reports.”
#
“You stand in for no one, as most games have you do – play for yourself, make your own decisions, and see the world react – if you’re leaving a trace that is.
Hacknet has no protagonist, other than the person using it. Don’t be reckless though – it’s more real than you think.”
#
#Hacknet(OS)’s commands are based off of actual UNIX commands, Hacknet is not your average TV Show or Hollywood Movie Hacker game. Hacknet is something diffrent, something more real. Hacknet uses a realistic Terminal, GUI (Menu), Netmap, some sort of Memory/Task bar. The most realistic feature of the game has to be the Terminal as you wouldnt really have that GUI in real-life hacking. If you dont know already, the Terminal is case-sensitive (in real-life and in Hacknet) so make sure you spell everything correctly! There are a couple of ways you can make hacknet more realistic just by changing how you play the game. Hacknet’s GUI is also customizable.
If you still dont really get it, try wathcing some Lets Plays on Youtube (or play it yourself!).
#
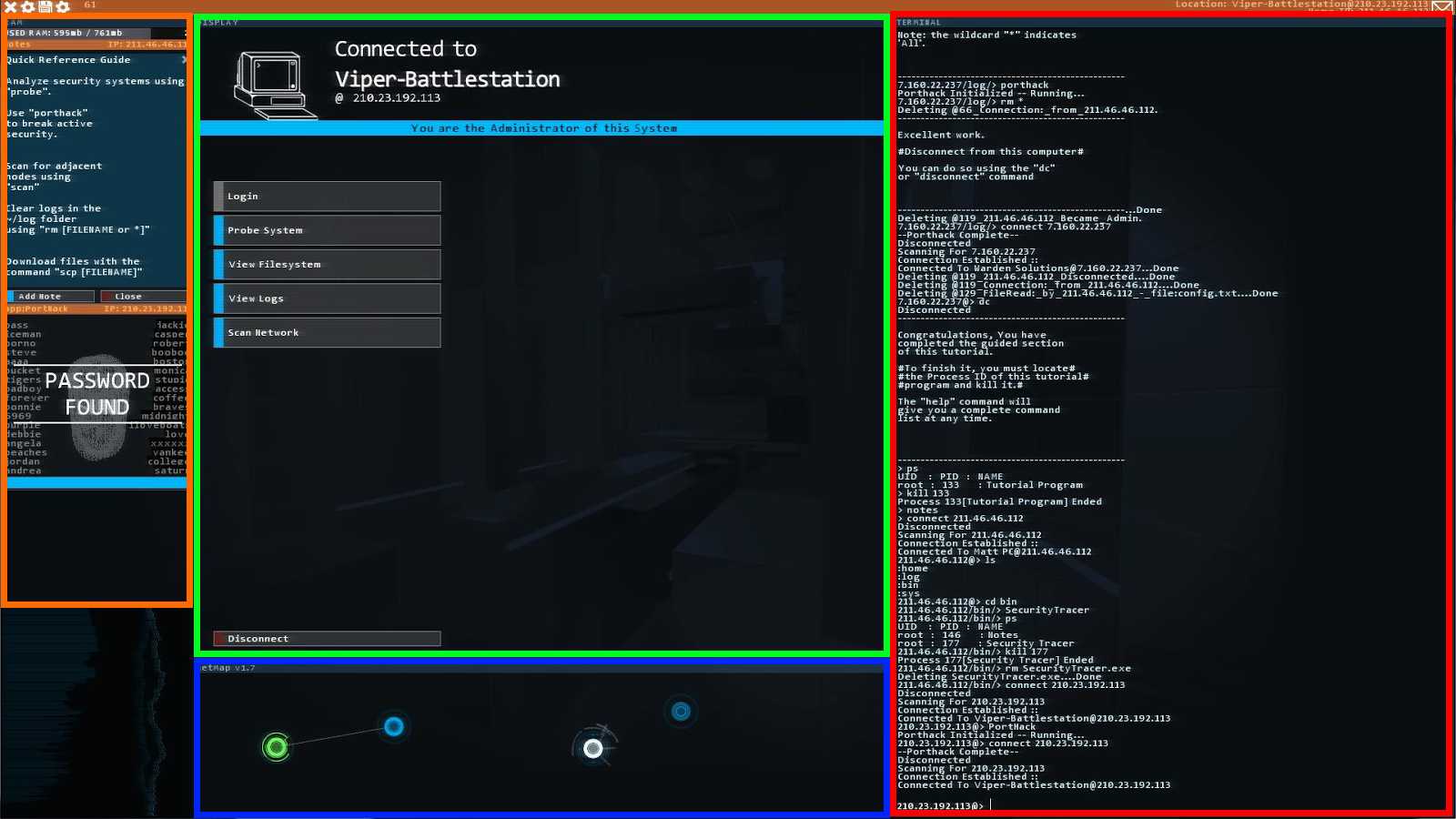
#Click the screenshot to zoom in for a better view!
Inside the Red Box is the Terminal.
Inside the Blue Box is the Netmap.
Inside the Green Box is the Menu,
and inside the Orange Box is the RAM/Task bar
#
~/home/Features.txt
#The GUI consists of a Terminal, Netmap, Menu, and RAM/Task bar.
Allow me to explain those a bit more…
#

###########################################################################
Example (In the Terminal):
123.456.7.8>cd log (Navagaiting to the /log folder)
123.456.7.8/log> ls (List all Files and Folders inside this Directory below the executed command)
—————————————————–
@log57803 123.456.7.8 BECAME_ADMIN
@log64375 123.456.7.8 File_Copied StuffUNeed.txt
—————————————————–
123.456.7.8/log> rm * (rm will remove a certian file, BUT if the wildcard * is used, it will delete ALL files inside that folder or directory without needing a filename.)
———————————————————–
Deleting @log57803 123.456.7.8 BECAME_ADMIN….Done
Deleting @log64375 123.456.7.8 File_Copied StuffUNeed.txt………….Done
123.456.7.8/log>
###########################################################################
As you play the game, you will be using the terminal 70-80% of the time, but if you dont touch the Menu at all then call it 90% of the time.
————————————————————————————————————————–

————————————————————————————————————————–

Through out the game you will most likely be using both the Menu and the Terminal. In some Missions, more than the other. Let me map this out for you. The Menu is pretty much a Display.
#
- Using the Menu, you can:
- Probe
- Login
- View Filesystem
- View Logs
- Scan Network
- Disconnect from computer
#
What you CANT do using the Menu: - Actually hack into the system
- Use/Run .exe’s or Hack Programs on Port Numbers
- Edit or Create Files
- Move Files or Folders
#
So, anything you can and cant do in the Menu, you can do in the Terminal.
————————————————————————————————————————–

~/bin/Trace.docx

#
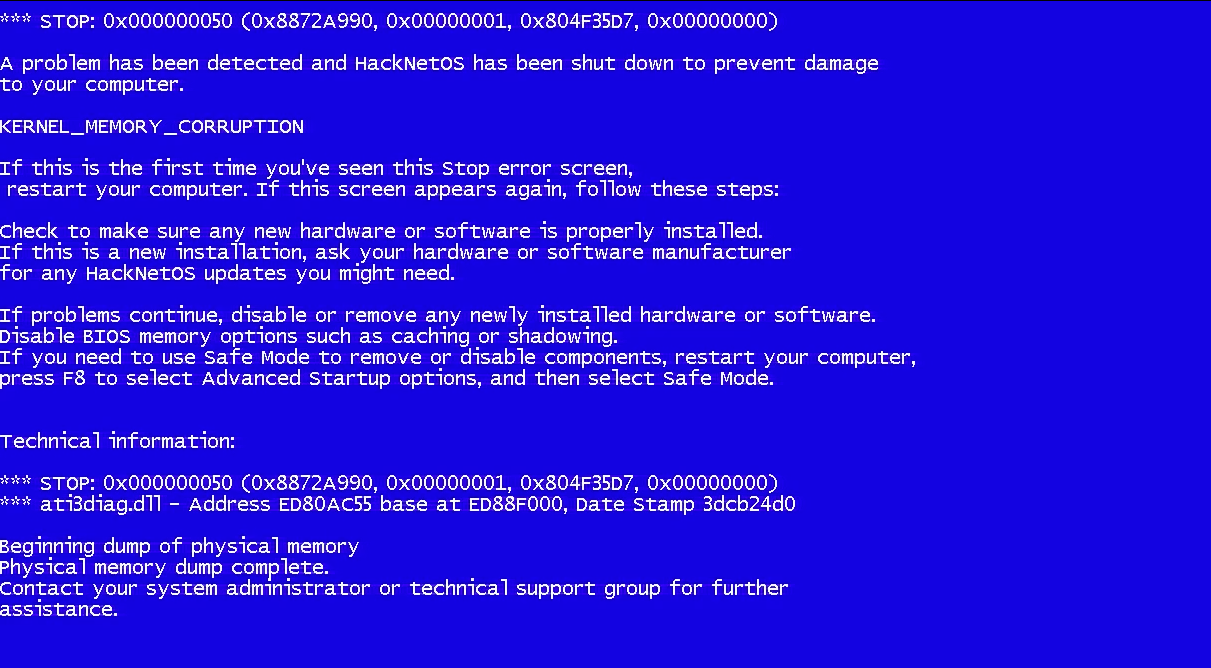
Your HacknetOS/In-Game Computer will crash. You will get whats called a “Blue Screen Of Death” or “BSOD” for short. Don’t worry, this screen is shown for about 5 seconds then your In-Game Computer reboots. However, there are certian computers that will complete the Trace and you will have a chance to hack into the ISP Mainframe to change your IP.
On some Computers, it is possible, but most computers in Hacknet.. No. There is a .exe/Executable you can get further in the story to stop the Trace, but it requires you to first hack into the system before you can launch it as it takes up A LOT of RAM. If you (somehow) have the Admin Login, use it. You will save youself a lot of time and effort.
That’s a big no. You will not lose any of your data (such as files) after the trace and BSOD.
~/bin/SSHCrack.exe
SSHCrack.exe is the first executable hacking program/tool you will get when you complete the first couple Jobs for Bit. SSHCrack has to be one of the fastest (in my opinion) exe’s you will get in Hacknet. It takes up a Fair amount of RAM, but you will be able to run other exe’s as well.
Time to Complete Task: N/A (For now)
RAM Usage: 246 MB
Uses Port: 22
Chance of Use: Very Likley
Obtained: Start/Early in-game